Apple wants to further customize your App Store(s) experience, according to a new patent at the US Patent & Trademark Office. Patent number 20110010759 involves providing a customized interface for an application store.
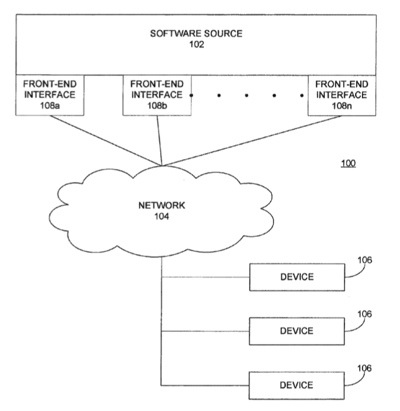
Embodiments of the present disclosure provide a system and method of providing customized access to an electronic storefront for downloading software for a mobile device based on authorization data stored on the mobile device. In one embodiment, mobile devices have stored one or more profile. Each profile is signed by a particular entity (a particular developer or enterprise) and includes authorization data authorizing one or more devices to install and use software associated with the entity.
A content management application associated with the storefront (e.g., iTunes) identifies one or more storefronts associated with the entities of authorized profiles for a particular device upon access to the storefront and provides the entity storefronts to a user of the device based on the authorization data stored on the device. In one embodiment, a profile is authorized, e.g., using encryption and installed to the device by the particular entity. Software for which distribution is limited to those authorized by an enterprise or other entity is thus only available for download to a properly profiled and authorized device. The inventor is Mitchell Adler.
Here’s Apple’s background of the invention: “Modern computing devices, such as computers, mobile computing devices, and mobile phones, are capable of downloading and installing a wide variety of software applications. For example, software sources, such as Apple’s App Store, allow users to browse and download applications onto their computing devices. For example, Apple’s App Store and others like it allow users to download various applications to their mobile devices, such as their mobile phone. Currently, there are an extremely large number of applications available through sources like the App Store.
“Different users and computing devices, however, may have different requirements regarding how these applications execute. For example, computing devices may be configured to require that any code executed be authorized by a trusted party. As another example, certain applications may be deemed unsuitable or unsafe for a particular user. Unfortunately, due to the extremely large number of applications, it can be difficult to manage the availability and installation of these applications.”
— Dennis Sellers