Apple plans to make it easier to share info between Macs and iOS devices, as evidenced by a patent (number 20110047598) for device identity matching at the U.S. Patent & Trademark Office. The technology is related to identifying devices based on their owner, and more specifically related to recognizing commonly owned devices, and devices owned by contacts, to authorize network connections between the devices.
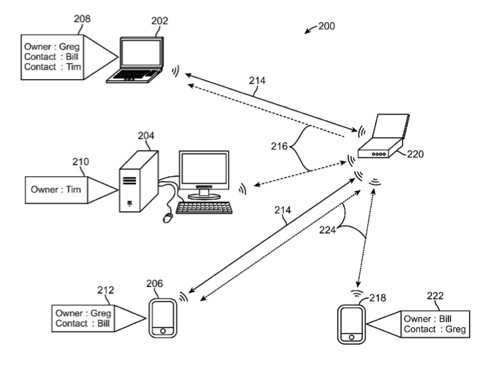
Per the patent, devices are identified by their owners and authorization to network two or more devices is based on device ownership. Data structures such as address books can store information about an owner of a device and maintain an entry indicating that a particular entry identifies the owner of the device. Other entries in the address book are contacts of the owner.
A host device can authorize a client for communication with the host based on a relationship between the owner of the client and the owner of the host as indicated by the presence of the contact information of the client’s owner in the host’s address book. Devices and can enable communication and sharing of services and levels of access permissions based on the relationship of the owners’ of the respective devices. The inventors are Gregory Charles Lindley, William Martin Bachman and Timothy B. Martin.
Here’s Apple’s background and summary of the invention: “There is a wide variety of electronics and other devices available on the market. Many of these devices attempt to make the lives of their respective owners (or users) easier, more convenient, and more enjoyable. It is common for a device owner to own and use multiple devices. For example, a device owner may use his/her desktop computer at home, laptop computer at work, and smartphone during commute.
“It is important for one device to be able to share information with other commonly owned devices. For example, a device owner may need to share pictures or documents amongst his/her desktop computer, laptop computer, and smartphone. A device owner may often times rely on more than one of his/her devices in the ordinary course of daily life. As a result, many device owners are becoming more attached to their devices.
“With this increasing reliance on electronic devices where devices become a part of users’ everyday lives, there is a need for these devices to be more personal. Typically the closest a device comes to being associated with its owner is through an owner account, or an owner identity field, or name of a profile on a device. However, an owner account typically associates a number or a SIM card with an owner on a server computer; the device does not know of the owner’s personal identity.
“The same is true with an owner identity field which has the result of inserting the owner’s name or contact information on wallpaper so that the device can be returned when lost, or inserting the owner’s name in comment bubbles or forms to be filled out or to name a device on a network, e.g., ‘Sam’s MacBook Pro.’
“Due to this deficiency, a device cannot identify itself or other devices by their owners absent some additional user steps that associate various accounts as being related. Even then, the nature of the relationship might not be clear. Owners have personal attributes, friends, and preferences.
“A need exists for devices to learn about the personal attributes, friends and preferences to enable new authentication techniques, and to permit users to switch devices without needing to create new authentication certificates, to identify a friend’s devices nearby, to automatically configure devices owned by the same person to work together, and to facilitate other benefits stemming from identifying an owner to a device.
“The present disclosure describes methods and arrangements for accepting communications from a second device based on the ownership of the second device. A first device can receive a communication request from a second device. The communication request comprises information identifying the owner of the second device so that the first device can authorize the requested communication based on the ownership of the second device. If the owner of the second device is represented as a contact in an address book stored on the first device, the first device can authorize communication by sending configuration information to the second device to enable the second device to connect to the first device.
“In some embodiments the owner of the second device is the owner of the first device. Since both devices are commonly owned, sharing of information about the owner’s preferences and characteristics can be desired and this sharing can be accomplished as part of the configuration information or a separate communication.
“In some embodiments, the owner of the first device differs from the owner of the second device; thus, the ownership of the two devices is diverse. An owner can have a plurality of contacts, stored as entries in the address book. In some embodiments, access permissions can vary by contact and information about the level of access permissions can be stored along with the contact’s information in the address book.
“In some embodiments, the host device can offer different services and this information can be communicated via the configuration information or a separate communication. Examples of these services can include sharing of location information, instant messaging, file sharing and other services.
“Additionally, a system for authenticating a client device for communication with a host device is disclosed, including at least one client device having a memory configured to store vcards. The vcard can be used to identify an owner of the client device by including contact information for the owner of the client device.
“The system further comprises a host device having a memory configured to store vcards. Again, the vcard can identify the owner of the host device. Vcards can also identify contacts of the host device’s owner. The host electronic device further comprises a communications interface configured to receive a communications request from the client device, and a processor configured to correlate the owner of the client device with the owner or contact identified by one of the vcards stored in the memory of the host device. Upon a positive correlation the processor can be further configured to authorize communications with the client device.
“A computer readable medium storing computer executable instructions for implementing a method on a device is also disclosed. The computer readable medium comprises computer code for instructing a device to receive data comprising information identifying a owner of the device and detect the presence of a second device on a network having the same owner, and establish trusted communications with the second device based on the common ownership of the two devices. In some embodiments a service discovery protocol is used to detect the presence of the second device on the network.
“Also contemplated is a device comprising a memory configured for storing an address book having information associated with contacts that includes a flag identifying one of the contacts as the owner of the device. The device further comprises a network interface configured for receiving information about other devices on a network and a processor configured for running a service discovery protocol controlling the network interface to receive information about services offered by and ownership of other devices on the network. The device is further configured for initiating a connection between the devices, and for accepting a connection request with one of the other devices on the network based on a positive correlation of the ownership of the other device and the entries in the address book.
“Additionally, a method of initiating communications with a host device is disclosed. A client device can send a communication request to a host device. The communication request can optionally be sent after the client device recognizes the host device having a recognized owner as broadcast by a service discovery protocol. The communication request comprising information identifying the owner of the client device as a contact of the host device. The client device can receive configuration information from the host device if the host device recognizes the owner of the client device as a contact of the owner of the host device and configuring the client device to operate in accordance with the received configuration information.”
— Dennis Sellers