According to a new research report, only 34% of users without email security responsibility recall seeing email-based attacks in their inboxes, compared to 85% of email security professionals.
The finding is part of the “2018 Email Security: Trends, Challenges, and Benchmarks” report released by GreatHorn, a cloud-native email security provider. Throughout June 2018, 295 business professionals from both technical and non-technical job roles were surveyed to gain a better understanding of the current state of enterprise email security, threat prevalence, remediation frequency, and importance within the wider security landscape.
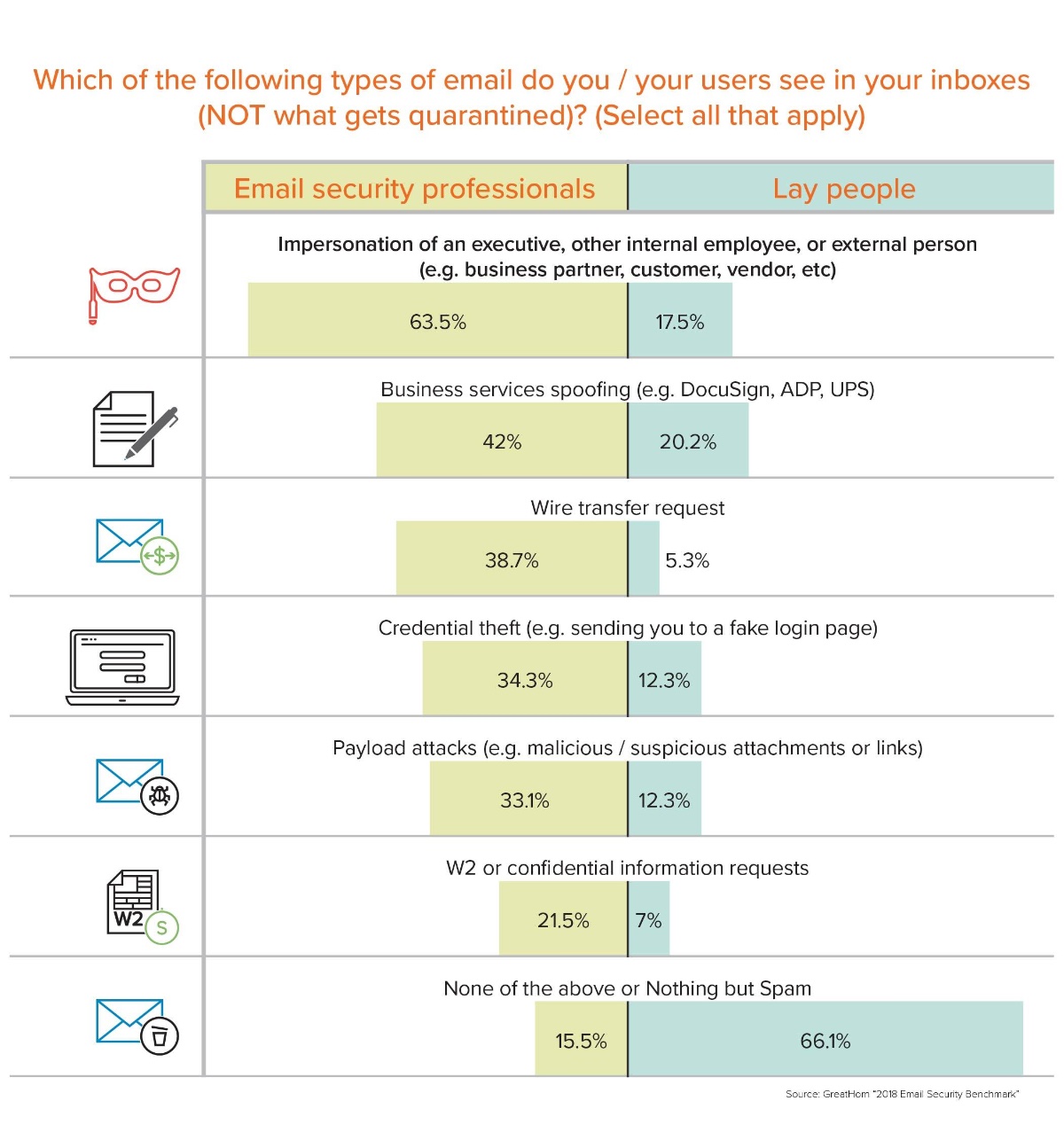
The data shows a perception gap around email security, particularly between email security professionals and other personnel. While two-thirds of non-security workers claim to never see any email threats besides spam, 56% of security professionals see email threats, including impersonations, wire transfer requests, W2 requests, payload attacks/malware, business services spoofing, and credential theft, on at least a weekly basis. What’s more, 20% of these same people also report a weekly need to take significant remediation actions to counter the effects of an email-based attack.
“The primary email security challenge enterprises face is trust,” GreatHorn CEO Kevin O’Brien says. “Our latest data shows that professionals mistakenly believe that their work email systems are inherently secure. In turn, this means that they are highly susceptible to phishing and social engineering attacks, especially as those attacks become more and more sophisticated. What’s needed is a security posture that begins with the assumption that some amount of malicious mail will always find a way to bypass legacy perimeter solutions, and which can intelligently identify, alert on, and disarm attacks that reach the inbox. The future of email security will be cloud-native, post-perimeter, and easily deployed – in other words, everything that yesterday’s solutions are not.”
Nearly half of all respondents (46%) were less than “satisfied” with their current email security solution, with only 10% indicating they were “very satisfied.” Senior-level IT and security personnel roles were much more likely to be actively “dissatisfied” or “very dissatisfied” by their email security solution (20% compared to 12% for the general population).
Forty percent of respondents need to routinely take significant remediation actions to counter basic attacks that get through their email security solution. Nearly two-thirds (65%) indicate experiencing major technical issues with their existing security solution such as the following:
° One in six miss basic payload attacks, despite being arguably the most heavily guarded against threats by perimeter-based email security solutions;
° Thirty-fie percent report that their current solution doesn’t stop internal threats (e.g. if a user account is compromised);
° Nineteen percent report that they have weak or no remediation capabilities if an email threat reaches an end user;
° Twenty-one percent believe their solution negatively impacts business operations (e.g. too many false-positives);
° Twenty percent are missing phishing attacks such as impersonations.
Overall, nearly half (46%) of all respondents see executive, internal, or external impersonations, with that number jumping to 65%among email security professionals. Business services spoofing was the second most prevalent email threat respondents experience (42%), followed by wire transfers (39%), credential theft (34%), and payload/malware (33%).
The FBI recently reported business email compromise attacks are responsible for more than $12 billion in losses in the past five years, so it’s no surprise that email security is a major focus for senior-level IT and security leaders. Fifty-four percent of respondents that were responsible for their organization’s security strategy selected email security as one of their top three security initiatives in 2018.