The global pandemic has seen a huge rise in people working from home, shopping online, and generally being more digitally connected than ever. There are plenty of good things that have come from this but there is a lot of bad as well.
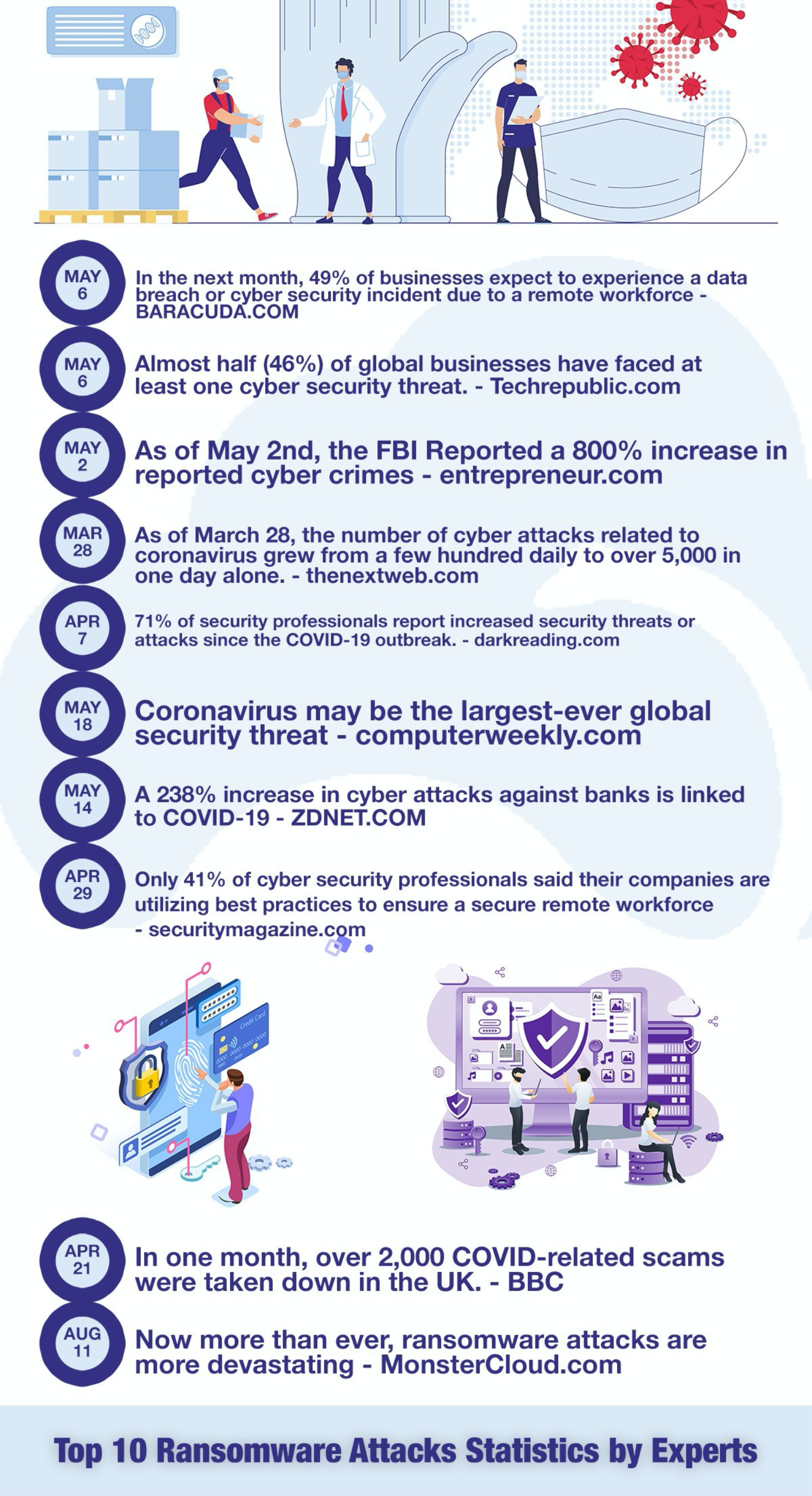
One of the biggest issues is that cyberattacks have skyrocketed during this period, according to MonsterCloud, a company that specializes in cyber terrorism and ransomware recovery. Cybercriminals have taken this opportunity to up their attacks, both in frequency and scope.
The FBI reports that the number of complaints about cyberattacks to their Cyber Division is up to as many as 4,000 a day. That represents a 400% increase from what they were seeing pre-coronavirus. Interpol is also seeing an “alarming rate of cyberattacks aimed at major corporations, governments, and critical infrastructure.” These attacks are targeting all types of businesses but large corporations, governments, and critical medical organizations have been major targets.
Certain types of attacks are up even more. Microsoft reports that COVID-19 themed attacks, where cybercriminals get access to a system through the use of phishing or social engineering attacks, have jumped to 20,000 to 30,00 a day in the U.S. alone. Zohar Pinhasi, a cyber counter-terrorism expert and founder of the cybersecurity firm MonsterCloud, reports that ransomware attacks are up 800% during the pandemic. Pinhasi told CBS News, “From those criminals’ perspective, it’s heaven. They have stepped on a gold mine.”
Ransomware attacks, where cybercriminals hold your computer data or network hostage until a ransom is paid, have been successful during the pandemic on a level not seen before, according to the folks at MonsterCloud. The hackers have gained control of major companies’ systems and demanded large ransoms. Exactly how much data was compromised, and if the ransom was paid has not been officially released but it seems like these attacks have been large.
In early June 2020, Honda announced that its Customer Service and Financial Service divisions were having technical difficulties and later confirmed that it was cyber attack-related. In July, Garmin users reported widespread outages which the company would later say was the result of a cyberattack. It has been reported that the attack is thought to be the work of the Russian group, Evil Corp. And, in August, Canon was reportedly attacked in a ransomware attack by the Maze ransomware gang in an attack that stole “10 terabytes of ‘data, private databases, etc.'”
Cybercriminals have also set their sights on another type of target during the pandemic, companies that are vital in the fight against the virus. These companies are so stressed and busy doing the all-important work trying to stop this global pandemic that they have become easier targets. They also hold incredibly valuable data such as research or potential vaccines that other companies or governments would love to get their hands on.
Starting in the early days of the global lockdown in the spring, the FBI issued warnings about cybercriminals targeting coronavirus research. These issues have turned out not only to be true but to be something that grew as the pandemic continued. In July 2020, cybersecurity officials from the U.S., UK, and Canada issued a warning about a hacker collective called APT29 and their “efforts to target U.S., UK, and Canadian vaccine research and development organizations.”
The most well-known and highly-publicized attack during the pandemic is the Twitter hack. On July 15, someone took control of several celebrities, business executives, companies, and politicians’ Twitter accounts and conned people into sending Bitcoin to an account. The attacker hacked into the accounts of people such as Apple, Bill Gates, Kanye West, Elon Musk, and even Barack Obama. The scam netted around $117,000 but ultimately led to the arrest of a 17-year-old hacker in Florida.
According to reporting by the Wall Street Journal, the attack was carried out by the perpetrator using a combination of traditional hacking, such as phishing sites, and social engineering. The hacker was able to take control of a cell phone number by convincing a carrier to assign a number to a new phone (this is known as SIM-swapping) and by convincing a Twitter employee (who was most likely working from home) that he was a Twitter IT employee.
This social engineering allowed the hacker access to sensitive information that allowed him to carry out the attack. It should also act as a warning to companies that cyberattacks are not always committed 100% online. The physical security of access to information can be just as important as cybersecurity, says MonsterCloud.