According to Wired (a subscription is required to read the article), a group of computer scientists have discovered a security vulnerability with the Apple Vision Pro that allowed them to reconstruct what folks were typing, including passwords, PINs, and messages.
According to MacRumors, Apple addressed the issue in visionOS 1.3, which was released in July.
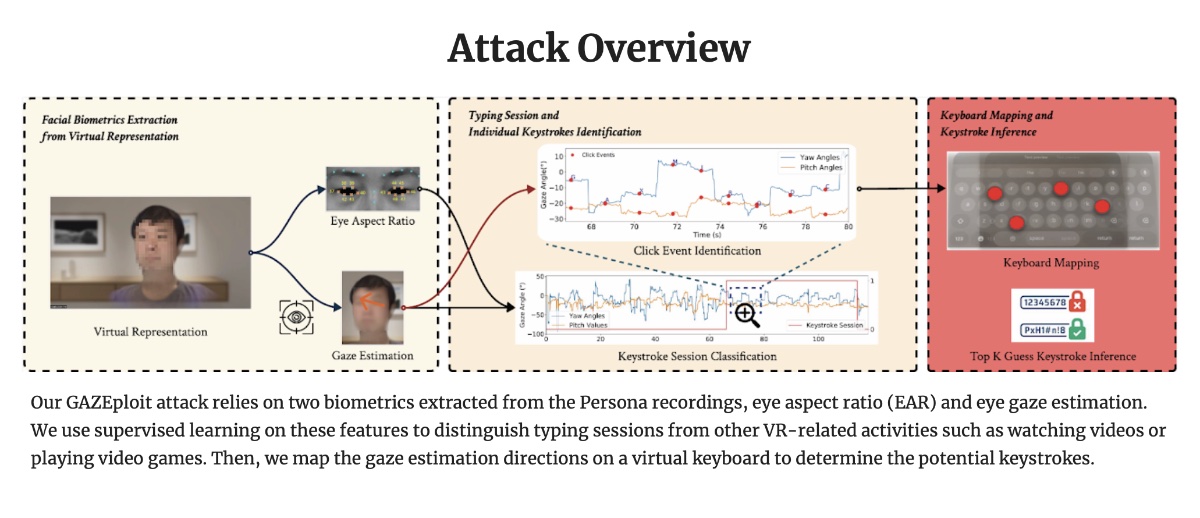
Regarding the vulnerability, when a user of the spatial computer was using a virtual Persona avatar, such as during a FaceTime call, the researchers were able to analyze the Persona’s eye movement or “gaze” to determine what the user was typing on the headset’s virtual keyboard. The researchers created a website with technical details about the so-called “GAZEploit” vulnerability.
From the website: The GAZEploit attack leverages the vulnerability inherent in gaze-controlled text entry when users share a virtual avatar. Virtual avatars, whether shared through video calls, online meeting apps, live streaming platforms, or potentially malicious websites, pose a significant privacy risk by potentially exposing user information such as login credentials. By remotely capturing and analyzing the virtual avatar video, an attacker can reconstruct the typed keys. Notably, the GAZEploit attack is the first known attack in this domain that exploits leaked gaze information to remotely perform keystroke inference.
Article provided with permission from AppleWorld.Today